Everything nowadays revolves around the control over personal information, where it is stored and who can use it as a possible source to fight against systems and organizations. In our next event, we will investigate the importance of digital sovereignty, its borders and technology used to collect information and also how to protect it.
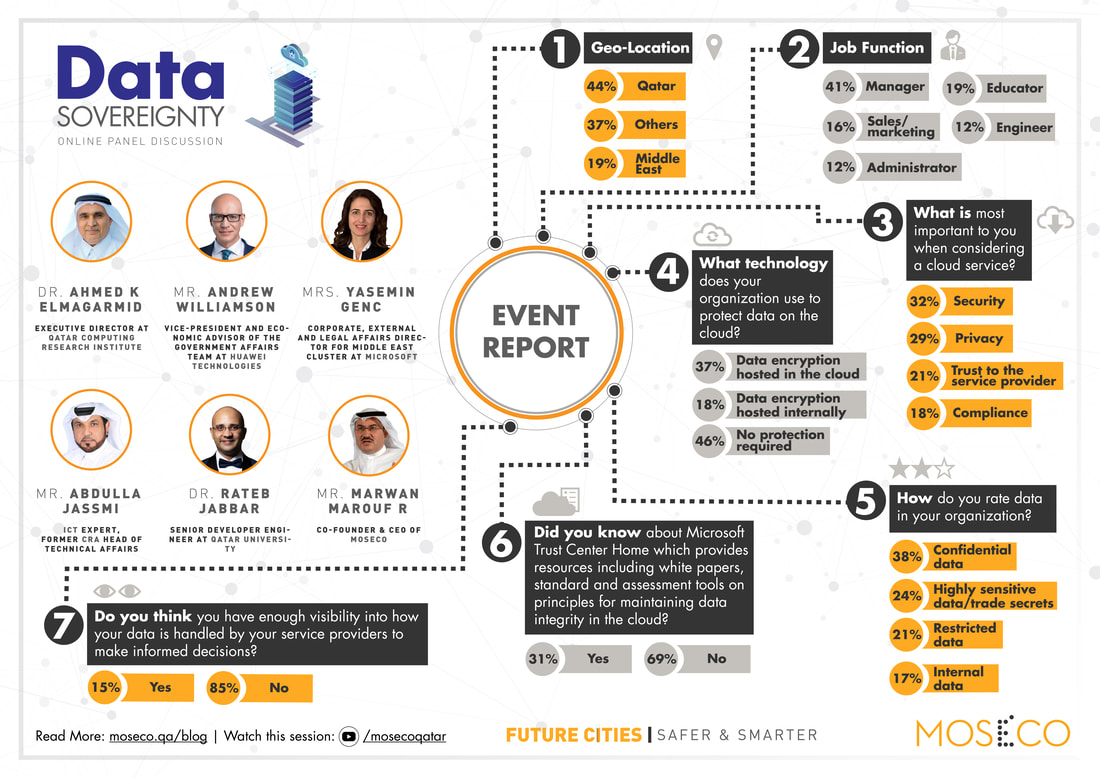
Together with our panelists, we discussed the availability of large pools of data, and infrastructure for using and exchanging data, but also the importance of appropriate governance rules and regulations. Data has become the new currency for countries to do business, and we have to be ready to face all the challenges pinpointing the location of the users’ data, taking control of at least their data sovereignty issues, which also includes better visibility into the clouds they use and computing platforms of effective data management.
We explored what has been done in other countries and see how this is relevant for Qatar, and where we stand in the digital sovereignty map, in order to helping us write our own manifesto in setting down the laws on data protection and sovereignty.
Together with our panelists, we discussed the availability of large pools of data, and infrastructure for using and exchanging data, but also the importance of appropriate governance rules and regulations. Data has become the new currency for countries to do business, and we have to be ready to face all the challenges pinpointing the location of the users’ data, taking control of at least their data sovereignty issues, which also includes better visibility into the clouds they use and computing platforms of effective data management.
We explored what has been done in other countries and see how this is relevant for Qatar, and where we stand in the digital sovereignty map, in order to helping us write our own manifesto in setting down the laws on data protection and sovereignty.
Trailer |
Highlights |
Full video |
|
|
|
|
|
Check out our latest blog post:
|
Download the panel PowerPoint presentation below
|